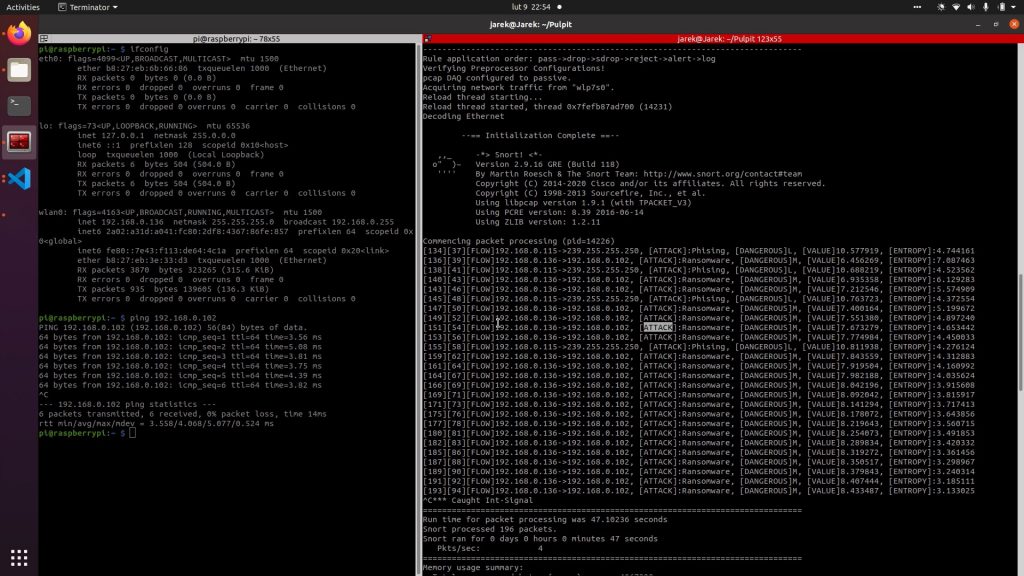
The SNORT module is Network Intrusion Detection System based on Snort environment. However, this tool contains extended functionality of Snort: heuristic approach to intrusion detection based on external data. We developed this prototype because we believe the joint approach to attack detection (in federation or just a group of entities in selected sector) is more effective than an individual approach.
Snort as an environment is a free open source Intrusion Detection System capable of logging and analysing incoming network traffic in real-time. Open source model of Snort engine allows us to increase the functionality of intrusion detection using heuristic algorithms. The crucial elements of Snort architecture allowing to implementation of new functionalities are the pre-processor.
SNORT module supports multivariable heuristic approach to intrusion detection. These variables can be personalized based on external data from third parties (e.g. federated entities in a specific sector). The user can influence the operation of the heuristic detection algorithm. The functionality of the prototype is based on new pre-processors added to the Snort environment. The global parameters of detection algorithm are:
- base value of a detected packet,
- lower limit of the packet value (threshold),
- upper limit of the packet entropy value.
Another preprocessor is used to configure the values of individual flags. The flags can describe the nature of a threat. Flags with their default values are described below.
- dangerous – identifies the severity of the threat associated with an IP address (e.g. High, Medium and Low). The value of this flag is subjective and depends on the environment in which the tool is used.
- attack – specifies the type of attack in which the IP address was recently involved (e.g. Phishing, DDoS, Ransomware, XSS, etc.). The value of this flag may differ from the environment because the effectiveness of an attack also depends on the purpose of the network and who is using it.
- range – describes the impact of an attack by an IP address on other network components such as a server, a switch or a router. In this case, a given attack may affect only a single attacked network component or spread over a part or all of the infrastructure.
- access – Some attacks (e.g. phishing, malware) require user action within the network, others (e.g. DDoS, DoS) do not require user intervention. This type of flag describes the need for user activity within the network.
- availability – Some attacks, such as ransomware, cause partial or complete loss of access to the unit and data on it. This type of flag describes the impact on the availability of the attacked component.
The final value of the packet should depend on the value of each flag in the appropriate proportion and the value of entropy. The final decision is based on the final value of a given packet.
More information about the SNORT module can be found in articles [1-3].
[1] Marcin Niemiec, Rafał Kościej, Bartłomiej Gdowski, "Multivariable Heuristic Approach to Intrusion Detection in Network Environments", Entropy 23, no. 6: 776. 2021. https://doi.org/10.3390/e23060776
[2] Bartłomiej Gdowski, Rafał Kościej, Marcin Niemiec, "Heuristic-based Intrusion Detection Functionality in a Snort Environment", Information & Security: An International Journal 50, no. 1 (2021): 23-36. https://doi.org/10.11610/isij.5010
[3] Bartłomiej Gdowski, Rafał Kościej, Marcin Niemiec. "Federated Approach in the Snort Environment – Towards Heuristic-based Intrusion Detection", Springer CCIS series [under review], 2022.
If you wish to know more about SNORT, watch the demonstration video on ECHO's YouTube channel here:





