As technology evolves, cyber-attacks progressively become more sophisticated and innovative. For an organisation or a corporation to repel or mitigate an upcoming attack, cyber threat intelligence (CTI) plays a decisive role through the collection, classification, and exploitation of knowledge about adversaries that gives defenders the upper hand and allows them to learn and evolve with each intrusion they face. Evidently, having access to accurate and comprehensive CTI enhances the preparedness, attack mitigation, and diagnostic capabilities of an organisation.
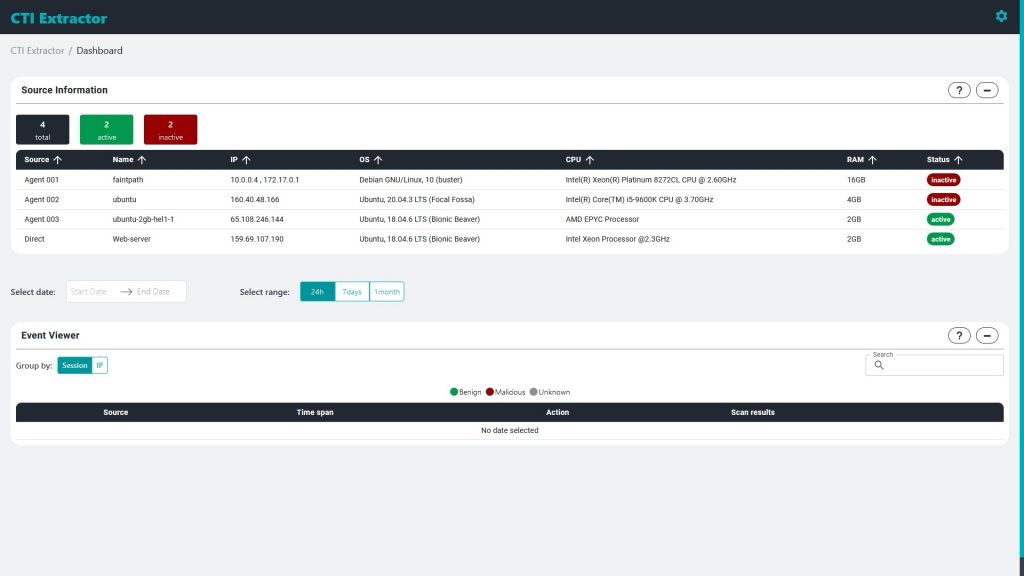
CTI extractor is a tool that aims at the extraction, analysis and correlation of CTI from internal sources. Such sources include, but are not limited to, web servers, database servers, but also network and application logs in general.
The CTI extractor tool presents complete contextual and technical details related to the security events that take place in any monitored system such as indicators of compromise and background details, as well as Tactics, Techniques, and Procedures (TTPs) used by the cyber adversaries targeting organisations or their subsidiaries.
Powered by a novel machine learning-based algorithm, but also conventional rule-based detection, the tool is able to identify critical threat indicators, present them in a flexible and intuitive web interface for data mining, analysis, and visualisation, and facilitate timely and accurate decision support. It also leverages the investigative capabilities of external tools by offering integration with OSINT platforms, such as Spiderfoot, but also the Malware Analysis and Intelligence Tool (MAIT) developed for the European network of Cybersecurity centres and competence Hub for innovation and Operations (ECHO).
In summary, the CTI extractor tool offers the following capabilities:
· Collects data from different internal sources using the settings provided in each monitored system's configuration;
· Aggregates and processes logs, and groups them into sessions;
· Extracts information related to security events using a signature-based approach that employs a set of rules via regular expressions;
· Identifies threats based on pre-defined and custom rules, but also is able to detect new threats using a machine learning-based engine;
· Offers detailed insights of findings, presents telemetry of key statistics, and provides a comprehensive view of the threat landscape affecting a monitored system; and
· Seamlessly integrates with external sources and analysis tools to further enrich the collected intelligence.
If you wish to know more about CTI EXTRACTOR, watch the demonstration video on our YouTube channel:





