For cyber security risk assessment, we mean the process of identifying risks, analysing them and evaluating the impacts on an organization. Without this process, an organization could waste time and money (effort) focusing for example on useless assets. One of the key points that a risk assessment tool should be to optimize investments to reduce the overall risks.
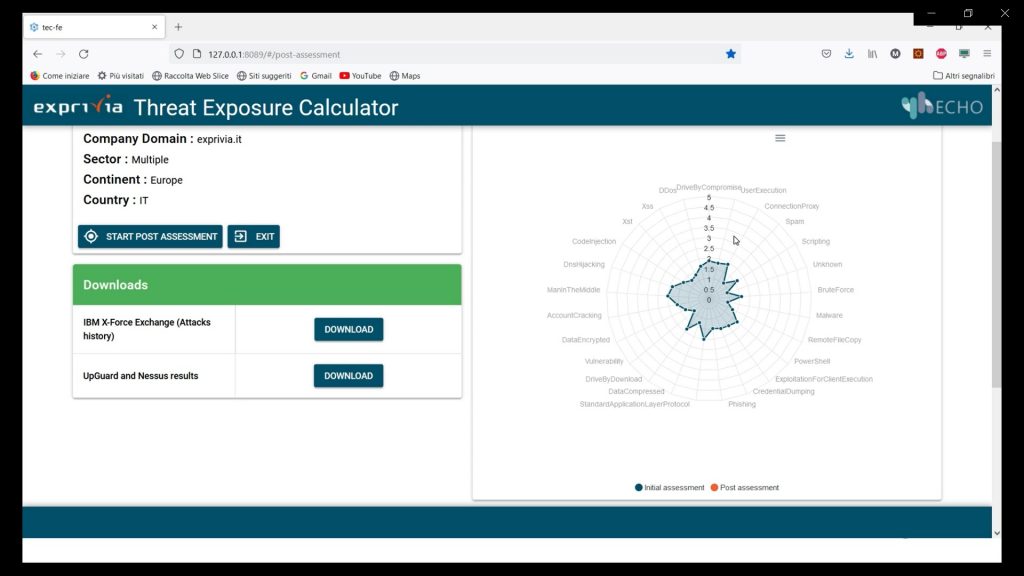
The TEC aims to calculate the current level of exposure concerning the main threats and subsequently to promptly provide targeted solutions tailored to the customer. The evaluation of the actual security situation is obtained starting from a passive analysis of the customer and an active interaction with the IT specialists.
The passive analysis is performed using tools designed to identify vulnerabilities regarding the web portals owned by the customer. This analysis is carried out exclusively from the external perimeter of the corporate network and is capable of monitoring vulnerabilities visible from the outside. Alternatively, the analysis that requires the intervention of IT specialists aims to investigate the security mechanisms implemented in the internal perimeter. Customer questions will range from CSIRT-compliant security services to vulnerability management.
After this data has been collected, the prototype reports the actual level of exposure to threats viewable in a radar chart, based on the main threats in that business sector and proposes solutions in terms of technology and security measures that must be adapted. The sectors involved in this analysis are:
- Cloud
- Critical Infrastructure
- Entertainment
- Finance
- Healthcare
- Multiple Sector
- PA
- Research / Education
- Retail
A state of the art analysis has been conducted, to identify similar tools and market needs. Most of the lacks of the tools are:
- Depends on the manual intervention of IT Specialist that need to fill a static questionnaire. The goodness of the analysis depends on the goodness of the question in the questionnaire.
- Obsolescence of the questions, the cyber threats are continuously changing and the questionnaire and the analysis should be updated frequently.
- Obsolescence of the analysis, because they are usually in specific period and consist of just a single snapshot.
- Ambiguous interpretation of the results.
The TEC addressed these market gap by providing the functionalities described above. In particular according to the previous bullet points:
- It uses automatic tools to reduce the manual intervention, and let the IT Specialists focus on a subpart of the analysis.
- The automatic external tools integrated analyse the perimeter according to the latest threats
- The analysis can be executed according to a schedule and then repeated more and more times without further intervention of humans. Alerting methods based on threshold on specific measures can be easily implemented
- The analysis is conducted the CyberSecurity Framework [CSF], a framework created by NIST (National Institute of Standards and Technology) intended to manage and mitigate cybersecurity risk.
If you wish to know more about TEC, watch the demonstration video on ECHO's YouTube channel here:





